SafeLiShare Enhances Security with Confidential Containers on Azure
The SafeLiShare Secure Data Platform now runs on Confidential Containers in Microsoft Azure. Microsoft Azure has recently introduced confidential containers on Azure Container Instances (ACI) that enable containerized applications to be executed on confidential VMs.
Confidential Computing is a term coined by the Confidential Computing Consortium (CCC) that refers to the protection of data by enabling computations on the data to be performed in a hardware-based Trusted Execution Environment (TEE) by authorized code only. This means that any code outside the TEE is prevented from accessing or reading the protected data or the code executing inside the TEE, ensuring that cloud service providers and any other actors are prevented from accessing the data and code being protected.
TEE implementations use PKI (Public Key Infrastructure) to provide a hardware root of trust, which is a set of private keys embedded in the hardware itself, and whose corresponding public keys reside in a manufacturer’s database. The integrity of a TEE can be ascertained (“attested”) by using its hardware root of trust, and the identity of the code running inside a TEE can be ascertained (“measured”) by using its cryptographic digest.
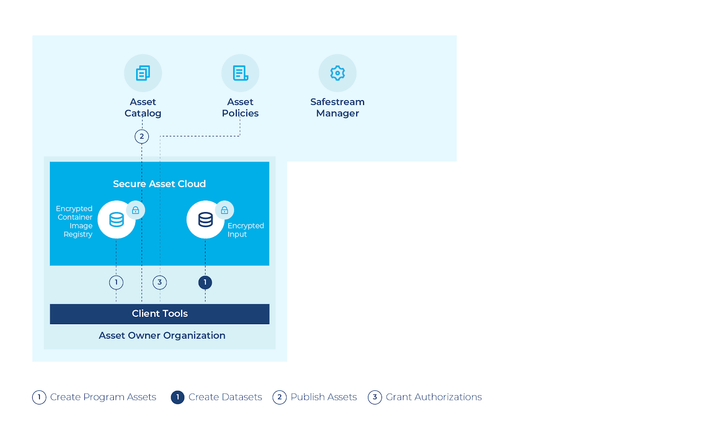
The SafeLiShare Secure Data Platform uses confidential computing to enable shared data and code assets to be created and published by their owners. These assets can be encrypted and when published, they use TEE-based PKI technology, which means they can be said to be “encrypted to the TEE”.
Access control authorization policies are used to ensure that only authorized parties can access the published assets, and a distributed authorization mechanism is used to enforce the specified policies. Policy enforcement determines whether published assets can be “stitched” together into potential executions or federated workflows called “SafeStreams.”
"Most modern processors are already TEE compliant making normalization of secure enclaves across processors a possibility in sight.” said Dr. Cheng Wu, General Partner at Taiwania Capital who is also the lead investor of SafeLiShare. “This paves the era for large scale confidential computing. Safelishare is at the forefront of that new wave."
Full Spectrum of TEE Compatibility
SafeStream Manager launches an execution using a cluster of TEE-enabled machines. Since the protections offered by the various TEE implementations vary, the SafeStream Manager needs to be aware of these differences and manage the execution specifications, PKI-based keys (“secrets”), and policy constraints accordingly.
For example, if the trust boundary extends to the process level, as in the case of Intel’s SGX, the SafeStream Manager ensures that no other concurrently executing process can read or access the protected data and code. Using confidential contaienrs in ACI, the trust boundary can consist of a container group. On the other hand, if the trust boundary exists at the VM level, as in the case of AMD SEV-SNP and Intel TDX, the SafeStream manager ensures that the protected code and data cannot be accessed by other VMs.
The SafeStream Manager also manages the PKI-based keys or “secrets” used to encrypt and decrypt the data and code assets. This involves ensuring that the keys are securely managed and distributed only to authorized parties.
Finally, the SafeStream Manager enforces policy constraints to ensure that only authorized parties can access the published assets and participate in the execution. This involves using a distributed authorization mechanism to enforce the specified policies and determine whether published assets can be used with each other in a computation. The computation can be set of containers and are together referred to as a Safestream.
When using confidential containers on ACI to run the SafeStream, the SafeStream manager creates a Confidential Computing security policy using a confidential computing enforcement policy that describes the algorithmic code assets, data assets, and other sidecar containers that execute inside the confidential container group. This policy specifies which code and data assets are allowed to execute inside the TEE and ensures that only authorized parties have access to the assets. The policy also enables the platform to release keys to the confidential container if the measurements can be attested. This helps ensure that only authorized code can access the protected data and code inside the TEE.
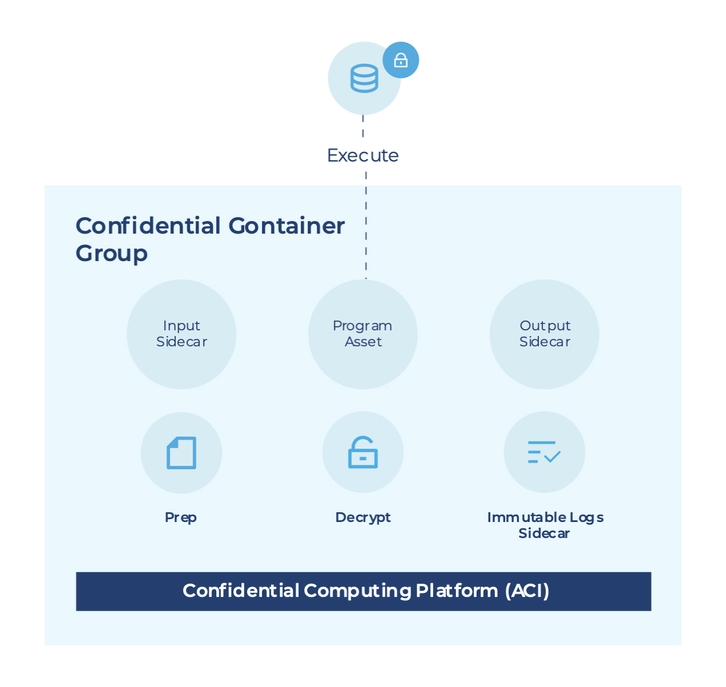
The picture below shows a simple confidential container group that runs an input container, a program container, and an output container. The input container pulls encrypted files and sends them to the program container, which consumes the input data and performs some processing. The output container then takes the output from the program container and writes it to storage.
The confidential container group also has a sidecar container that logs all the activity inside the containers into an immutable log. This helps ensure that all activity inside the containers is traceable and auditable automatically, which is important for security and compliance purposes.
SafeLiShare Use Cases on ACI
SafeLiShare extends PKI (a standard) to mitigate algorithmic complexity attacks and prevent unauthorized access in OWASP Top 10 without any proprietary PKI extensions.
Eliminate Attack Surface of Algorithmic Complexity Attacks
An algorithmic complexity attack is a type of cyber attack that exploits vulnerabilities in an algorithm or program by inputting large amounts of data or complex inputs that cause the program to consume excessive amounts of resources, such as memory or processing power. This can cause the program to crash, , allowing the attacker to gain unauthorized access or disrupt normal operations. Algorithmic complexity attacks are often used in denial of service (DoS) or supply chain attacks and can be difficult to detect and prevent. Attacking a program running inside ACI instance does not give the attacker access to memory outside of it, thereby isolating breaches.
By preventing algorithmic complexity attacks and providing decentralized identity management to algorithmic objects or apps, SafeLiShare can elastically enable large scale single party or multiparty data sharing with data protection provided by Azure confidential computing.
Uncover Application Runtime Security without Human Oversight
With the decentralized authorization and asset-based authentication in a TEE, SafeLiShare can prevent software development lifecycle (SDLC) breaches and rogue admin access to supply chains by automating the native hardened security controls with any compromises such as code leaks, hardcoded secrets, & misconfigurations. It prevents illegal use and unauthorized application access.
“As the industry drives towards confidential computing as a new standard, the implementation with the confidential containers on Azure Container Instances give a glimpse into a future where Azure can provide and manage infrastructure, SafeLiShare can provide solutions, and both can be technically verified to not have any access to the data being processed.” said Graham Bury, Principal Product Manager, Microsoft Azure Confidential Computing.
Immutable Logs and Auditability
Compliance ready auditability and access control including automatic privacy compliance of data assets can be greatly simplified and automated with SafeLiShare’s TEE compliance. SafeLiShare use cases can also be divided into single party and multiparty computing and confidential data access in banking, insurance, healthcare, financial, manufacturing, gaming, SaaS data access and more. With the hardware-generated tamper-proof logs, confidential computing can minimize privacy risks during project collaboration.
Privacy Preserving Multi-Party Data Analytics and Access
Confidential computing enables secure data processing between multiple organizations by enabling them to provision encrypted input data into a confidential container that can prevent outside access the data. This capability is useful in data collaboration scenarios such as fraud detection and secure healthcare data analysis.
Encrypted data from various external sources can be loaded into a ACI and decrypted data is only visible inside the container. Upon request, the ACI container will conduct computation or processing on the data without any involved parties being able to view each other’s data and provide agreed upon results to the output owner.
For more information on SafeLiShare’s use case with confidential containers on Azure Container Instances, design architectures, or access log examples, contact info@safelishare.com or visit here.
Experience Secure Collaborative Data Sharing Today.
Learn more about how SafeLiShare works
Suggested for you

February 21, 2024
Cloud Data Breach Lifecycle Explained
During the data life cycle, sensitive information may be exposed to vulnerabilities in transfer, storage, and processing activities.

February 21, 2024
Bring Compute to Data
Predicting cloud data egress costs can be a daunting task, often leading to unexpected expenses post-collaboration and inference.

February 21, 2024
Zero Trust and LLM: Better Together
Cloud analytics inference and Zero Trust security principles are synergistic components that significantly enhance data-driven decision-making and cybersecurity resilience.