Decentralized and Distributed Authorization Explained in Confidential Computing
Authentication and authorization are two important tools used to protect systems and information. Authentication verifies the identity of the user and authorization determines what users can access or what actions they can take.
Safelishare Dynamic Secure Data platform enables data assets from one domain to be processed by algorithmic objects (code assets) from another domain using a Trusted Execution Environment. The data and the code assets may be created in different domains and published. Specific entities such as organizations and accounts may be granted access to published assets using policy specification languages such as OPA/Rego.
Centralized vs. Decentralized
Issues such as certificate fraud, fake credentials, slow verification processes, tight coupling between multiple domains, and data breaches are prevalent in centralized digital identity and authorization systems.
When a client attempts to log in, the server checks the credentials supplied against a hash kept in its database. If they match, an authorization policy is looked up and applied to that session. At other times, the client contacts an authorization server directly, getting a token verifying both authentication and authorization, which it passes on to the service provider. This architecture poses two core issues: one, the central service is a major risk with one attack able to put many user accounts in danger; two, whoever operates the central server has complete visibility of all users’ private permission data.
A decentralized identity and authorization scheme can solve certain issues, offering various benefits to users.
Organizations issuing credentials and authorizations can provide fraud-resistant documentation while verifying organizations are able to quickly confirm the validity of such documentation. As multiple administrative domains are part of the process, this system ensures that unauthorized access is restricted. Each domain only needs to be aware of the permissions from its own domain.
Individuals have full control over their digital identity and authorizations, without having to rely on any centralized party for validation.
Distributed Authorizations allow credentials in one domain to be generated and permissions of an asset to be tracked in an immutable store. This graph-based store can also prove the authorization cryptographically so that it can be independently monitored and not coupled to each domain’s storage.
Identity-Based Encryption (IBE) and an immutable log database can be employed to create a Distributed Authentication and Authorization Service (DAAS), where digital signatures are utilized to verify the identities of owners, assets, and their permissions in a distributed manner. Verifying these authorizations using code executed in a Trusted Execution Environment (TEE) ensures that machine-level policies are kept separate from the cloud service provider.
Identity-Based Encryption and Private Key Generator
Identity-Based Encryption is a part of the suite of Identity Based Cryptography tools in which some known attribute of a user Alice (e.g., email address) can be used to derive a public key. The corresponding private key is then generated by a trusted entity called the Private Key Generator (PKG). Any sender may then use Alice’s public key to send an encrypted message that can only be decrypted by Alice using her private key.
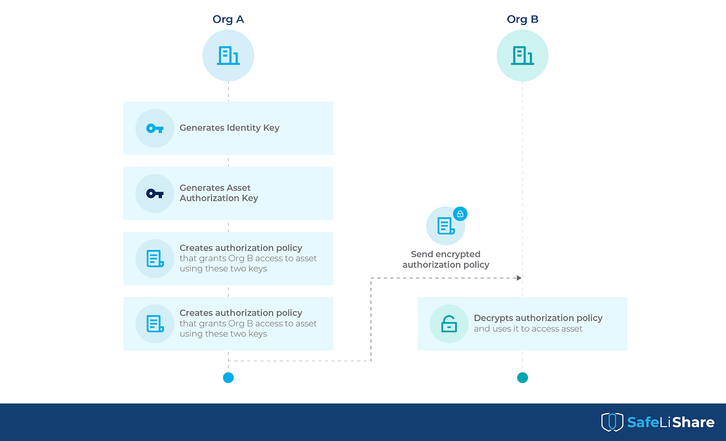
- Org A creates an authorization key to be used to decrypt the authorization policy.
- Next, Org A creates the authorization policy using the authorization key and signs it with its identity key to form an IBE-based authorization.
- This authorization is further encrypted using the public key of Org B.
- Thus, only Org B can decrypt the authorization policy (using its identity-based private key).
Variants of IBE may be used to express sophisticated authorization policies, e.g., policies regarding expiration dates and times.
The authorizations legs of the graph are encrypted and stored in an immutable repository that can be distributed. When an asset needs to be accessed, its associated cryptographic proofs can be generated from the asset owner to provide the necessary proof from the immutable log. Since authorizations can be proved without access to the permission store a third party can validate the authorizations and act as a proxy for providing access. A Secure TEE can play the role of this trusted proxy of transferring access to assets between two domains after validating the authorizations. Thus we can create a collaboration platform between two(or more) domains without the platform having access to the assets in those domains.
Summary
Decentralized authentication and authorization allow organizations to have full control over the data they generate, preventing it from being distributed without permission, and addressing the existing illicit activity or unauthorized access.
The use of Trusted Execution Environment (TEE) systems, along with distributed authentication and authorization, can simplify and automate auditability, and access control with automatic privacy compliance of data assets. Additionally, TEEs allow for the creation of collaborative computing platforms while still preserving isolation among multiple administrative domains.
SafeLiShare enables secure access to confidential data stored across clouds by utilizing a Trusted Execution Environment — a secure enclave. It provides hardware-based policy access control and auditability, allowing for automated privacy compliance of data assets. For more information on SafeLiShare’s Secure Data Platform, email info@safelishare.com.
Experience Secure Collaborative Data Sharing Today.
Learn more about how SafeLiShare works
Suggested for you

February 21, 2024
Cloud Data Breach Lifecycle Explained
During the data life cycle, sensitive information may be exposed to vulnerabilities in transfer, storage, and processing activities.

February 21, 2024
Bring Compute to Data
Predicting cloud data egress costs can be a daunting task, often leading to unexpected expenses post-collaboration and inference.

February 21, 2024
Zero Trust and LLM: Better Together
Cloud analytics inference and Zero Trust security principles are synergistic components that significantly enhance data-driven decision-making and cybersecurity resilience.