The Confidential Computing Solution:Data and Workload Sharing
Confidential computing is changing the way businesses approach data and workload sharing. It’s an innovative way of protecting data and workloads as they are processed, enabling organizations to maintain control over sensitive data while gaining new benefits from collaborative cloud services. In this article, we’ll explain what confidential computing is, why it’s a transformative solution for data and workload sharing, and how you can use it in your business.
What Is Confidential Computing?
Confidential computing is a new method of secure computing, which provides an environment where user-defined or sensitive code and data are isolated from the execution environment. This means that all access to information (reading, storage, or modification) is explicitly controlled by the application running on the secure platform. By separating network elements and operating system/hypervisor from application logic and ensuring isolation at the hardware level, Confidential Computing allows users to trust their highly sensitive data with remote providers without ever revealing it publicly.
Benefits of Confidential Computing
Confidential Computing has deep implications on security, but also on other aspects such as scalability, performance, and privacy. Firstly, with Confidential Computing sensitive data can remain safe even when stored remotely in shared clouds managed by third-party providers. A Confidential Computing platform gives users total control over their private data so that it’s never revealed outside their organization’s boundaries — even if hosted in a public cloud run by someone else. Secondly, confidential computing offers a much lower chance of errors or malicious behavior because it’s isolated from underlying infrastructure making sure that records remain immutable through time. Furthermore, its ability to handle highly parallelizable structures makes it more efficient for large volumes of computation-intensive operations than traditional methods — thereby reducing costs for organizations who have complex computing needs involving multiple nodes distributed around the world. Finally, its high levels of encryption keep individuals’ private information safe -such as payment details- by providing state-of-the-art cryptographic algorithms (e.g., AES GCM). Given the vast amount of data in use from endpoint to the cloud, and the mounting pressures on securing that data, 96% of enterprise IT, security, and engineering executives agree that securing the broad spectrum of exposures with Confidential Computing would improve application security.
Applications and the sensitive data they process — data in use — are susceptible to unauthorized access and manipulation during processing. Data is usually encrypted at rest in storage and in transit across the network. Depending on where it is encrypted, even when it is encrypted at rest, either the data or the encryption keys may be open to unwanted access. According to Gartner, by 2025, 50% of large organizations will adopt privacy-enhancing computation for processing data in untrusted environments to protect data in use.
By implementing confidential computing, most enterprises hope to secure their data and assets to a degree where they can properly mitigate the legal and financial risk of potentially serious data breaches. Confidential computing protects data in use by isolating it within protected enclaves that cannot be accessed by platform administrators, service providers, or platform software, such as hypervisors. Furthermore, 91% of enterprise executives believe confidential computing can enhance innovation.
Using Confidential Computing For Data & Workload Sharing
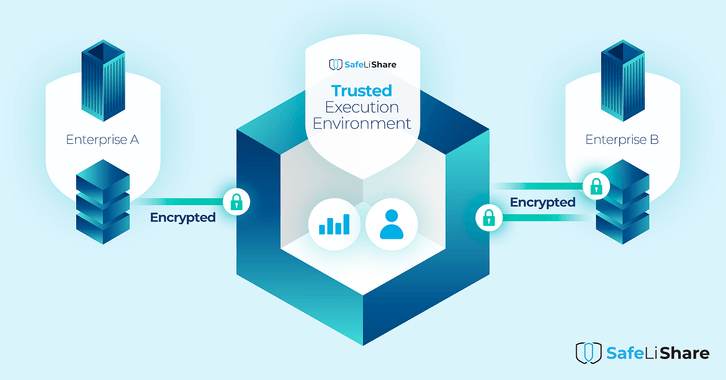
Confidential Computing provides users with an extra layer of security against malicious behavior or external interference that might affect shared workloads. It makes this possible by restricting access to resources through authenticated Identity & Access Management (IAM) systems — such as virtual token authentication based on MFA where only authorized personnel can access resources after authenticating through encrypted digital certificates — further ensuring that no one can tamper with your protected resources without explicit permission from authorized parties.
Additionally, to ensure security within workload sessions, applying cloud isolation capabilities will prevent potential configuration errors from leading to privilege escalation problems. SafeLiShare uses recent advances in confidential computing technology to provide Policy Driven Access to Applications and Data (PDAAD) throughout a workflow, i.e., to every stage/workload in the data flow. SafeLiShare support for audit and verification functionality is now possible with SafeLiShare’s PDAAD technology.
Bring Data to Compute
Many businesses keep large volumes of sensitive data out of the public cloud due to regulations or to maintain complete control, and so they miss out on the benefits that the cloud delivers, e.g., AI and big data analytics. Confidential computing is a key component in expanding the use of AI.
Secure enclaves are designed to safeguard data against attacks that take advantage of physical access to servers. This is significant because unauthorized entities in the context of confidential computing could include other applications on the host, the host operating system and hypervisor, system administrators, service providers, and the infrastructure owner — or anyone else with physical access to the hardware.
By protecting data in use, confidential computing enables companies to first bring sensitive data to the cloud and second combine data without giving each other access to that data.
One of the advantages of confidential computing is that it provides many levels of security, including the assurance that the code is running in an enclave you trust and has not been altered or tampered with. A process known as attestation allows changes to be detected by having the hardware generate a certificate stating what software is running. Unauthorized changes can quickly be detected. Developers can also choose various paths to TEE-enhanced security depending on whether they want it employed more quickly or want to custom-design their protection.
SafeLiShare encrypted clean rooms are, in essence, a series of interconnected secure enclaves that control and manage the keys used to decrypt the registered assets and control the ensuing computations. End-to-end protection for sensitive and private information brought into the clean room is ensured as assets are re-encrypted when exiting the clean room.
Bring Compute to Data
In order to secure confidential data as more businesses migrate their data processing workloads to the edge, edge platforms will need to provide confidential computing. Like cloud computing, the multi-tenant nature of edge raises privacy concerns for customers that can be addressed by confidential computing.
Confidential computing affords organizations in all industries a measure of confidence in the privacy and security of their data. The adoption of confidential computing to protect data — including all varieties of code artifacts — during processing is anticipated to increase as organizations move toward becoming digital enterprises and data becomes crucial to their operations. This is particularly true for technology companies. A number of cyberattacks, including advanced persistent threats, RAM scraping, and compromised system environments, all pose a significant risk to data that is left unprotected during processing. While confidential computing may not avoid speculative execution attacks, it does make them far more difficult to execute successfully.
This is due to the nature of confidential computing, which concentrates on encrypting data-handling processes using an encryption key generated and contained within the hardware itself, making it significantly more difficult for other processes to ‘break in’ and gain access to the data. This approach secures access to the data because encrypting the data would make it impossible to process.
Dynamic Application and Data Pairing
All the emphasis on data security and access should not preclude concerns with the algorithms/code that processes the data. Many enterprises spend vast amounts of resources on algorithm development and code generation. Recent advances in machine learning models and AI systems emphasize the importance of algorithm design, development, and code and application development. It must be remembered that a workload consists of data and code assets.
Many enterprises are now providing ML models and analytics applications for use in obtaining insights from data. Gartner and the Confidential Computing Consortium estimate that collaborative computing, in which data and application code are provided by two different parties (also known as multi-party analytics) is set to become a $54 Billion market by 2026.
In multi-party collaborative computing use cases, the concern of the analytics/code provider is to protect the Intellectual Property (IP) of its code asset (algorithm privacy) whereas the data provider is concerned with data security (data privacy).
In SafeLiShare’s system, both the data and code assets are uniformly treated with respect to policy specification and enforcement. Policies may be specified to protect code and data assets. By establishing secure links between code and data assets, SafeLiShare can ensure that only a predetermined code asset can be allowed to process a given data asset, and vice versa. Both data and code assets are encrypted when stored in clean rooms. As needed and based on authorizations, code, and data assets may be combined to define a workload.
When encrypted data and code assets comprising a workload are brought into a confidential computing secure enclave for execution, the encrypted assets are first decrypted using a key protected by the confidential computing hardware.
Unique Encryption in Use and Confidential Computing Approach from SafeLiShare
Confidential computing technology allows the creation of run-time environments, called secure enclaves, that assign encrypted memory space to user applications. Confidential
Computing hardware protects the keys used to decrypt the encrypted memory space assigned to applications. An application running in a secure enclave is isolated because no other application can access its encrypted memory space. Data is processed by an application running in a secure enclave, and the code of the application is protected from other applications that may be running on the same computer. SafeLiShare uses computer programs, called policy servers, running in secure enclaves to request and use encryption keys that may be used by data and application owners to encrypt their data and applications. The corresponding decryption keys are only made available by the policy server to applications inside an (attested) secure enclave.
The identities and credentials involved in the execution are recorded in logs that are generated by a known logging process that runs in a secure enclave.
Data exposure is further increased when applications run in network domains not under the control of the data owner such as in cloud contexts where the data owner does not control physical access to the network or computer processing the data. SafeLiShare uses secure enclaves based on confidential computing technology to manage data and application vulnerabilities by introducing Policy Driven Access to Applications and Data (PDAAD).
With SafeLiShare, data and applications remain encrypted using Policy Driven Access to Applications and Data (PDAAD) whenever security is necessary. Data can only be accessed (decrypted) within a protected and isolated secure enclave. Because the decryption keys issued to a program running inside a secure enclave are protected by the confidential computing hardware that produced the secure enclave, the secure enclave is the only and exclusive root of trust. Data and applications have specified ownership; usage of data or applications is only permitted by the owner or someone authorized by the owner.
If you would like to hear more about our innovation and patent overview, follow us on Linkedin or visit our website at safelishare.
Suggested for you
February 21, 2024
RSAC 2024: What’s New
SafeLiShare unveils groundbreaking AI-powered solutions: the AI Sandbox and Privacy Guard in RSAC 2024

February 21, 2024
Cloud Data Breach Lifecycle Explained
During the data life cycle, sensitive information may be exposed to vulnerabilities in transfer, storage, and processing activities.

February 21, 2024
Bring Compute to Data
Predicting cloud data egress costs can be a daunting task, often leading to unexpected expenses post-collaboration and inference.

February 21, 2024
Zero Trust and LLM: Better Together
Cloud analytics inference and Zero Trust security principles are synergistic components that significantly enhance data-driven decision-making and cybersecurity resilience.