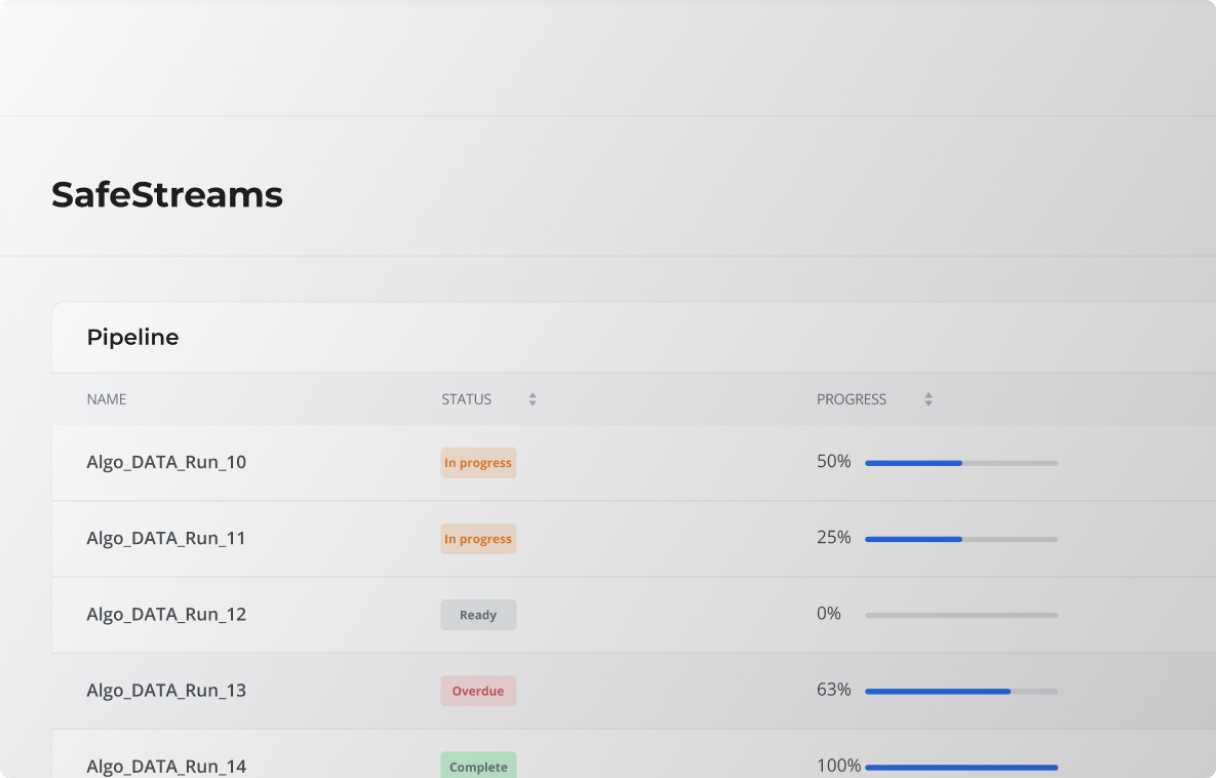
Confidential Analytics Platform Across Clouds
Modern enterprises live and die by their application and data. SafeLiShare makes confidential computing as simple as drag and drop coding to address security risks for critical applications and sensitive data.
SafeLiShare ensures policy driven access to applications and data within trusted execution environments, guaranteeing data privacy, and fulfilling data governance and compliance regulations.
Defend Your Business Against the Growing Risk of Insider Attack and Data Theft
Costly
USD 4.35 mil average total cost of a data breach. USD 9.44 mil average cost of a breach in the United States, the highest of any country.
Source: Cost of a Data Breach Report 2022 by IBM Security
Frequent
Nearly one-fifth of breaches were caused by a supply chain compromise with longer impact lifecycle.
Difficult to Detect
308 days on average to identify and contain a breach
Source: 2022 Verizon DBIR
The Solution
Enterprise Confidential Access
SafeLiShare stops the full spectrum of supply chain compromise and insider attacks with a fundamentally innovative data security service approach.
Data and application owners specify access, control, and compliance policies. Gain auditability, trackability and visibility of all accesses to your data.
- Data is always encrypted
- Data is only made accessible inside secure enclaves to authorized applications
- Verifiable audit logs are available for all workloads
Confidential Collaboration
Collaborate with partners or contractors in an inter-enterprise environment to gain the most from your data and applications.
Data in use is actively changing. With SafeLiShare, individuals and applications can process data in an encrypted or secured format. The runtime approach with federated workflows stops malicious internal and external attacks during data processing.
- Maintain data locality
- Maintain algorithm and intellectual property privacy
- Invoke protected workloads from external workflows (Airflow, BigQuery, Knative)

“SafeLiShare helps mitigate one of the major barriers to cloud adoption for highly-regulated application data assets, or with any organization concerned about unauthorized third-party access to data in use in the public cloud.”
Brendon Howe, VP/GM, Blockchain
VMware
How SafeLiShare Applies Zero-Trust Principles with Data-Centric Security to Protect Data and App Assets
Eliminates Costly and Sophisticated Supply Chain Attacks That Others Miss
Supply chain breaches were responsible for 62% of System Intrusion incidents in 2022 (Verizon DBIR 2022) - caused by behavioral profile of your users, organization, contractors and vendors.
Access to data and compute code is strictly orchestrated within SafeLiShare elastic secure enclaves. This enables stringent data security governance policies to discover, classify and protect sensitive data throughout its life cycle — both on-premises and in the cloud.
Security of Applications and Data
The platform prevents unencrypted application and data to be exposed at runtime to all other software by being processed directly in hardware encrypted secure enclaves.
Modern applications are increasingly modular, interconnected and exposed — SafeLiShare automates secure service provisioning and recognizing and enabling the integration of security into DevSecOps and SaaS.
Initiate Secure Enclaves with JSON Manifest
By running entirely inside a secure enclave, data owner’s cryptographic keys and application code are always protected and encrypted.
SafeLiShare mitigates one of the major barriers to cloud adoption for highly regulated businesses or any organization concerned about unauthorized third-party access to data in use in the public cloud.
Bring Data to Compute. Bring Compute to Data.
With SafeLiShare, no data is copied or transferred between accounts. The data is protected cryptographically and physically isolated for computation. In secure enclaves powered by SafeLiShare’s asset level policy control, even administrators can never access data they are not entitled to view.
In secure enclaves powered by SafeLiShare’s asset level policy control, even administrators can never access to data they are not entitled to view.
Integrates With Clouds, Data Aggregators and Security Operations
All security functions are supported as RESTful APIs, for easy integration to cloud-native tools and technologies.
SafeLiShare integrates into incident response processes and tools to help analysts respond to security incidents. It triggers playbooks and sends logs and metadata to SOAR, SIEM, and ITSM platforms.
Securing Application Data Lifecycle
Owner Encrypted assets on disk
Encrypted keys shared along with policies inside TEE's
Distributed entities
Encrypted Relationship-based access control (ReBAC) that can specify constraints for program and output enforced inside TEE’s
System encrypted output data accessible only to output owner
Decrypt programs only inside TEE's
Share encrypted data keys to only measured programs in TEE's and to a specific partner
Output is enforce to meet policy reas
TEE Memory in which decrypted data exists is NOT accessible to other programs even with root access
Collect
Verify data sources
Identity protected data
Create metadata
Assign ownership and policies
Store
Save data
Provide access to only approved actors
Share
Provide data to partners and program
Analyze
Run compute on data and produce putput
Manage Outputs
Provide access to outputs
Secure Data Platform Features
Hardware Attested Application Access Control
The SafeLiShare platform enables execution of client application programs inside TEE's after the enclave runtime successfully attests itself to the platform.
- Hardware assisted attestation provides identity of the client application
- Decryption keys are provisioned only after successful remote attestation
- Client application programs and Client Data are decrypted only inside TEE's
Elastic Encrypted Data Clean Room
The SafeLiShare platform enables creation of an abstraction called federation. A federation is a group of organizations that can share assets with each other in a data clean room.
- Enables sharing of data where programs can work on raw data to match with another organization to see the overlap between datasets
- Adjunct to their existing infrastructure and monetize assets that were previously private
- Automate the transfer of secure data to enable instant decision making and faster compliance
Immutable logs and insights
The SafeLiShare platform generates events from protected environments to append-only persistent logs. The logs are linked cryptographically to each other.
- Logs cannot be tampered with, i.e., they cannot be changed or deleted.
- Platform provides API's to store, retrieve and cryptographically verify the log events.
- Logs contain openenclave verifiable quotes that can be independently verified.
- Automate the transfer of secure data to enable instant decision making and faster compliance
Distributed Authorization for Asset Sharing
SafeLiShare uses a cryptographically enforced decentralized authorization system that can provide support for transitive delegation, offline participants and discovery of permissions.
- Organizations and users can delegate or revoke permissions they have delegated.
- Graph based authorization by creating signed certificates with grant of permissions
- Authorizations are enforced by secure enclave resident programs so they can be trusted
Encryption in Use
The SafeLiShare platform provides Encryption-in-use which ensures only authorized software (algorithms) can be securely loaded into memory and gets access to the data streams using hardware-based encryption and attestation schemes.
SafeLiShare’s confidential computing platform mitigates one of the major barriers to cloud adoption for highly regulated businesses or any organization concerned about unauthorized third-party access to data in use in the public cloud. It allows a high level of data confidentiality and privacy controls between competitors, data processors and data analysts
Data Residence and Sovereignty Assurance
By 2025, 60% of large organizations will use one or more privacy-enhancing computation techniques in analytics, business intelligence or cloud computing.
You can rest assured that your personally identifiable information (PII) and PHI will remain safe while never leaving the legal boundaries of your home jurisdiction.
CSP independant TEE trust policy enforcement
SafeLiShare policy enforcement is executed inside measured TEE environments and provides a cloud service provider independent policy specification and enforcement that is secure and private.
Policies are verified inside secure enclaves. The decryption keys are moved from key vaults and provided to programs after remote attestation of the secure enclave.
No-code RESTful API for Easy Data Integration
Enables organizations to share any encrypted GNU C Library based applications “safelets” to leverage different hardware based isolation techniques to support “encryption in use” without leaking private keys used to encrypt them.
- Runtime secure infrastructure service inserted through command line
- Upload script package through management portal
- Automate the insertion and integration in CI/CD templates
Persistent Data Loss Prevention (DLP) with Privacy by Design
Secure Enclave can help with DLP is by storing sensitive data, such as cryptographic keys or biometric data, securely within the enclave, making it much more difficult for an attacker to access or steal. Secure Enclave also provides hardware-based encryption and decryption of data, which adds an extra layer of protection against unauthorized access including in-memory or algorithmic complexity attacks.
It is designed to resist various forms of attacks, including side-channel attacks, which can be used to extract information from a system by analyzing the physical characteristics of the hardware. By preventing these types of attacks, Secure Enclave helps to ensure that sensitive data remains protected.
SafeLiShare Dynamic Data Security with Confidential Computing
- SafeLiShare extends PKI to prevent data leakage, algorithmic attacks and unauthorized access without any proprietary PKI extensions
- By preventing algorithmic attacks and providing identity management to algorithmic apps, SafeLiShare enables large scale enterprise or multi-party data sharing with confidential data security enforcement
- A compliant trust execution environment (TEE) implementation is considered FIPS 140-2 level 3 and 4 extensibility
People also ask
Who can see my data?
Where are the data assets stored?
Can the solution be hosted in our own domain/account?
Deeply Integrates With Data Analytics Ecosystem
Data Security Posture Management
Take the next step to secure data collaboration as organizations mitigate data security and privacy risks. Identifying meaningful data risk is impossible to solve without combining metrics from data sensitivity, data lineage, infrastructure configurations that create data risks and access risk into a common view.
SaaS Platform Data Ownership Assurance
Keep your SaaS data safe, secured and private with the help of modern data custodianship through secure enclaves and confidential computing.
Stop Supply Chain Attacks and Insider Theft Today
Protect your organization from the full spectrum of data security and stop unauthorized third-party access to data in use in the public cloud.
Additional materials
February 21, 2024
RSAC 2024: What’s New
SafeLiShare unveils groundbreaking AI-powered solutions: the AI Sandbox and Privacy Guard in RSAC 2024

February 21, 2024
Cloud Data Breach Lifecycle Explained
During the data life cycle, sensitive information may be exposed to vulnerabilities in transfer, storage, and processing activities.

February 21, 2024
Bring Compute to Data
Predicting cloud data egress costs can be a daunting task, often leading to unexpected expenses post-collaboration and inference.

February 21, 2024
Zero Trust and LLM: Better Together
Cloud analytics inference and Zero Trust security principles are synergistic components that significantly enhance data-driven decision-making and cybersecurity resilience.