Data Security Breach in 2023: To Date…
Data breaches have become increasingly common in today’s interconnected world — and this isn’t likely to change any time soon. Supply chain data breaches are serious events that can cause enormous financial losses, lead to customer data being compromised, and tarnish the reputation of companies whose systems were hacked.
In 2023, encryption will be a critical component in ensuring data security in the supply chain. Regardless of on-premises data centers to cloud-based infrastructure, monitoring your infrastructure, detecting threats, and maintaining cloud compliance and security is more important than ever as the attack landscape becomes more sophisticated and distributed.
Hackers are becoming increasingly clever at targeting vulnerable networks and workloads, making security breaches almost an inevitability. Even companies with state-of-the-art cybersecurity measures have fallen victim to advanced persistent threats and data breaches in recent years. And while there is no surefire way to protect against every possible cyber-attack, understanding emerging trends and recognizing potential threats are key components of staying secure in multi-cloud and multi-party distributed workflows.
According to IT Governance, there were 104 publicly documented security incidents, accounting for 277,618,767 leaked records. That’s more violated records than we discovered in any calendar month last year, and it’s among the highest number of incidents ever recorded.
T-Mobile
T-Mobile USA said on January 5 that an unidentified hostile intruder infiltrated its network in late November and stole data on 37 million users, including addresses, phone numbers, and birth dates. This breach identifies that most of the user data is on the cloud and was encrypted. T-Mobile agreed in the earlier year, in July 2022, to pay $350 million to consumers who filed a class action lawsuit after the company revealed in August 2021 that personal data such as Social Security numbers and driver’s license information had been taken. Nearly 80 million Americans were affected.
A data leak comprising the email addresses of over 200 million Twitter users was sold for $2 on a famous hacker site. Threat actors and data breach collectors have been selling and distributing massive data sets of scraped Twitter user profiles comprising both private (phone numbers and email addresses) and public data on different online hacker forums and cybercrime marketplaces. These data sets were built in 2022 by exploiting a Twitter API vulnerability that let users enter email addresses and phone numbers to determine whether they were related to a Twitter ID. The threat actors then utilized another API to scrape public Twitter data for the ID, which they then paired with private email addresses/phone numbers to establish Twitter user accounts.
The vulnerability allows any party without any authentication to obtain a Twitter ID (which is almost equal to getting the username of an account) of any user by submitting a phone number/email even though the user has prohibited this action in the privacy settings. The bug exists due to the process of authorization used in the Android Client of Twitter, specifically in the process of checking the duplication of a Twitter account.
Attackers Acquire the user ID by using the API Vulnerability
Even though Twitter addressed this problem in January 2023, various threat actors have lately begun to release the data sets they gathered for free over a year ago.
Aflac Data Breach
Following a cyberattack on a third-party contractor, personal information for more than 1.3 million Aflac cancer insurance customers and over 760,000 Zurich Insurance auto insurance policyholders is now available on the dark web. In total, almost 3.2 million data records were accessed during the incident. The compromise affected around 1.3 million consumers who were registered in the company’s “new cancer insurance” and “super cancer insurance” contracts. The incident, which was created by a vulnerability in a file transfer server, was initiated by a subcontractor of a third-party vendor that Aflac Japan utilizes for marketing reasons. The data, which did not include personally identifiable information, was published on the dark web.
Aflac said it received information on January 9 that its customer data was circulating on the dark web after a hacker obtained the information from a U.S. contractor’s server on January 7.
Zurich Data Breach
Zurich Insurance revealed a similar data breach to Aflac Insurance that affected current and past clients of “Super Automobile Insurance,” a local insurance product.
However, The Zurich data breach exposed the PII and policy information of auto insurance clients. The data breach did not disclose the bank account information, credit card details, or accident information of the insurance policyholders. Furthermore, the global Swiss insurance business reported that the data hack solely affected Japanese insurance subscribers. The data leak, according to Zurich’s representative, did not damage the company’s core business processes.
According to Switzerland Times, a total data of 2.6 million customers, and 757,463 previous clients of a local vehicle insurance product were exposed. Last names, dates of birth, genders, email addresses, policy numbers, customer IDs, car names, grades, and other insurance-related information were among the details revealed in the Zurich data breach.
Anderson Corporation Data Leak
Andersen Corporation, a construction and home renovation company, exposed clients’ confidential information, including property photos and addresses. The Cybernews research team uncovered an unsecured Azure storage blob holding around a million files belonging to Renewal by Andersen, a subsidiary of the international Andersen Corporation, on January 18, 2023.
Nearly 300,000 cloud-stored documents revealed the company’s customer house locations, contact information, and home remodeling requests, as well as inside and exterior images of client homes in several US states. The earliest files are from 2016. Customers preserved renovation projects in the cloud storage, including JSON files with their names, emails, and phone numbers. The dataset also included a “savedata” file, which presumably included the hashed physical signature of the client.
Screenshot of “savedata” file containing signature hashes.
It also included PDF files including order specifics such as materials utilized, goods purchased and installed, numerous agreements, and images of residential regions where company employees intend to execute the operation. Researchers warn that such data leaks are risky because threat actors may use personal information such as names, emails, phone numbers, and addresses to commit phishing schemes, identity theft, and other forms of fraud.
Details regarding the repair work and photographs of the residences may render the victims more vulnerable to burglary. Furthermore, leaked physical signatures in the form of hashes might allow threat actors to impersonate the individual and fill out paperwork on their behalf.
Puma Data Leak
Private information reportedly belonging to over 230,000 Puma clients in Chile has been discovered on a hacker forum. A threat actor has posted for sale an 84MB dataset purportedly belonging to the multinational sportswear brand. The cybercriminal or criminals responsible for the dataset listing say it is from Puma’s Chilean e-commerce website.
Customers’ names and contact information, such as emails, phone numbers, and billing and shipping addresses, were included in the disclosed database. It also included information on their purchases, including order numbers, payment methods, the total amount spent, shipping expenses, and discounts.
Exposed Puma’s Dataset
The reported data loss at Puma is risky because it allows threat actors to run targeted phishing attempts. Thread actors might also utilize this information in conjunction with partial credit card information revealed earlier by the victim to purchase products with the victim’s card.
Prevention against the Data Leaks
These leaks could have been prevented by implementing unique encryption and proper authorization controls to block public access to confidential data and cloud storage. Here are the ways how companies can prevent data leaks.
Data Encryption
With the increasing amount and value of data being hosted in cloud environments, organizations should take steps to protect cloud-hosted databases. Most organizations planning data encryption deployments lack encryption key and secret management strategies, which increases the risk of data loss. You should minimize the number of encryption vendors where possible to simplify key management operations by leveraging multiple products from a single vendor that can be applied to multiple data protection use cases and business objectives. This can reduce crypto-jacking vulnerabilities and service secret management overhead. All data, including email, should be encrypted both “at rest” and “in motion” when not in use.
Use data classification schema to bring visibility into the cloud development lifecycle and reduce the volume of sensitive information that’s vulnerable to a breach. You can protect sensitive information by employing encryption-in-use technology available from SafeLiShare. Furthermore, using an internal framework for audits, evaluating risk across the enterprise, and tracking compliance with governance requirements can help improve your ability to generate predictive analytics, detect data breaches, and escalate containment efforts.
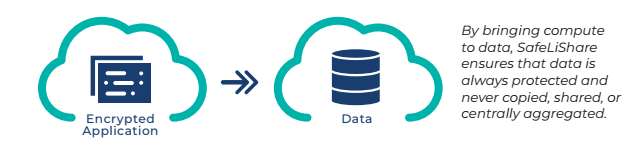
SafeLiShare allows encrypted data and encrypted applications to be “stitched” together and presented for execution inside a secure enclave. The execution needs keys for decrypting the application and the data from the policy server which are only provided if the respective identities of the application (and account credentials of the data and application owners) are verifiable. The identities and credentials involved in the execution are recorded in logs that are generated by a known logging process that runs in a secure enclave.
Bringing Compute to Data or Vice Versa
Gartner claims that by 2025, more than 75% of all enterprise data will be processed on the edge. That is a tectonic shift in the way businesses must build and think about their data systems. Edge computing will serve virtually all industries. Early leaders are being driven by the requirements of computationally intensive technologies such as computer vision.
Businesses may become considerably more aware and reactive to what is happening in their environments by shifting to the edge and bringing compute to data. As a result, businesses may gain new operational efficiencies and become more efficient with the resources they have.
SafeLiShare Brings Compute to Data.
Rather than move data between jurisdictions, SafeLiShare’s solution allows encrypted applications (‘compute’) to be moved to the jurisdiction where the data resides. It also allows encrypted applications to be moved across data and network domains, including across organizations. Application and data owners state policies governing the usage of their respective assets. These governance rules are enforced using SafeLiShare’s PDAAD (Policy Driven Access to Applications and Data) technology that also provides audibility, trackability, and visibility of all data accesses. To protect the application’s IP, as encrypted applications move to a new network domain, they always remain encrypted and cannot be accessed by any third party.
To join the data security as a service with SafeLiShare, follow us on Linkedin for more data security and confidential computing updates.
Suggested for you
February 21, 2024
RSAC 2024: What’s New
SafeLiShare unveils groundbreaking AI-powered solutions: the AI Sandbox and Privacy Guard in RSAC 2024

February 21, 2024
Cloud Data Breach Lifecycle Explained
During the data life cycle, sensitive information may be exposed to vulnerabilities in transfer, storage, and processing activities.

February 21, 2024
Bring Compute to Data
Predicting cloud data egress costs can be a daunting task, often leading to unexpected expenses post-collaboration and inference.

February 21, 2024
Zero Trust and LLM: Better Together
Cloud analytics inference and Zero Trust security principles are synergistic components that significantly enhance data-driven decision-making and cybersecurity resilience.