Privacy-Preserving Software-as-a-Service with Confidential Computing
Data protection and confidentiality are at the top of every security practitioner’s mind. To protect software and data assets from threats such as data theft, noncompliance, and attacks against applications, especially as more organizations move their data to the cloud. Understanding your rights and obligations under data protection laws and regulations is essential to ensuring compliance with the law — no matter what type of software service you’re operating.
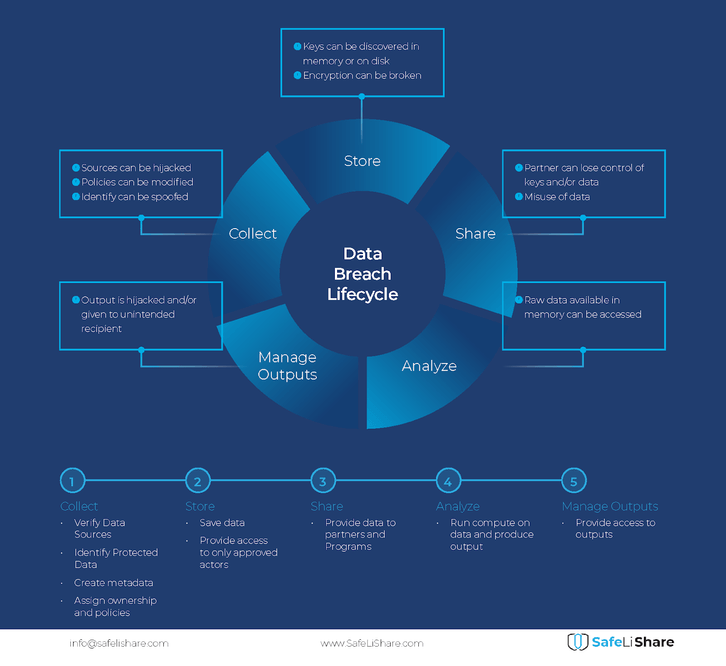
Data breaches have become a common occurrence, with organizations being increasingly vulnerable to cyber-attacks and malicious actors. Understanding the data breach lifecycle is essential for any organization looking to develop strategies to minimize the risks of theft or other unauthorized access to sensitive information.
Key measures for security and data protection in SaaS
Validation of secure configuration and interconnection of SaaS platforms is essential when running software in public clouds and allowing access to others.
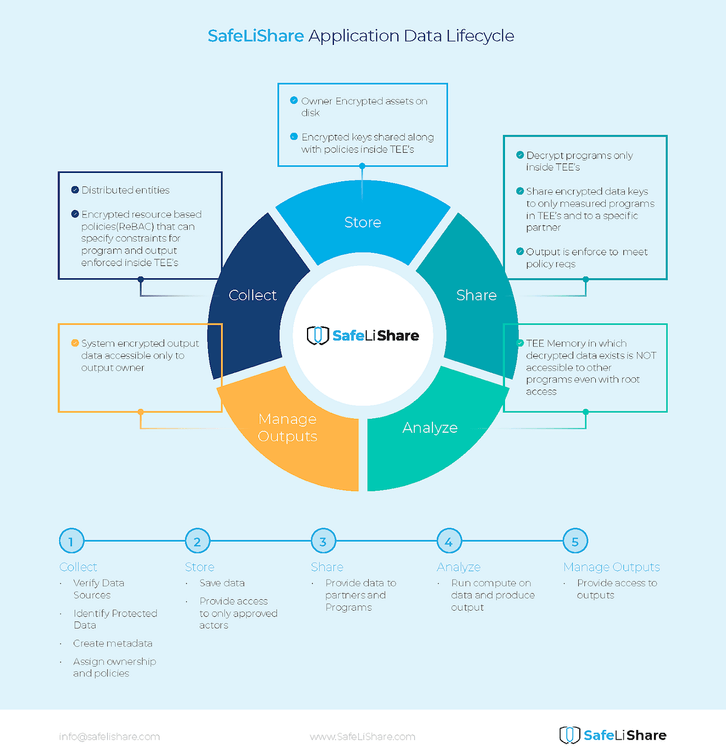
1. The Data Collection Phase
Organizations must ensure that the internal security measures they have in place are robust and regularly monitored. This includes user access control, verification of data sources, periodic audits of the system and monitoring logs going in and out of the SaaS platform. Protected data must be identified using, e.g., a Posture Management system, allowing attribute level control. Ownership and usage policies must be established for all data, including protected data.
When selecting a cloud-based data source, companies should investigate whether their security practices meet industry standards, such as ISO/IEC 27001 or the Cloud Security Alliance Cloud Controls Matrix (CSA CCM). Organizations should also request access logs to see who has had access to customer information.
2. The Data Storage Phase
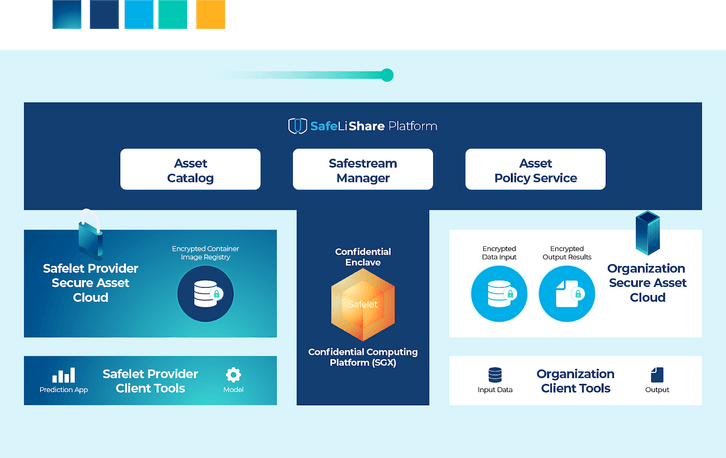
Organizations must ensure that the data in this phase is stored in encrypted form and the encryption keys are properly managed. One possibility is to use cloud-based vault systems for storing keys. For example, the SafeLiShare Dynamic Data Security platform uses client software to generate and store keys. The client software is completely under the control of the data owner.
3. The Data Sharing Phase
When providing data to partners and programs, organizations must retain control of the shared asset. Sharing need not imply loss of control and trusting the receiving entity to obey the data owner’s policies.
The first step in data sharing is to assign policies to the shared data that must be observed by the receiving partner or program. SafeLiShare’s platform allows policies to be specified that identify the organizations and accounts within those organizations that are authorized to process the data. Furthermore, program-level permissions may also be specified. This includes capabilities that assign a unique identity to programs and code assets that are cryptographically linked to the data. Such links prevent unauthorized programs from processing the data.
4. The Data Analysis Phase
It is one thing to specify policies that control access by programs and organizational entities and another to ensure that the specified policies have been executed.
The question is, how can the data owner ensure that the receiving program or entity obeys the specified policies? This is where the main power of confidential computing technology in the form of secure enclaves becomes crucial. Secure enclaves allow trusted executions of (shared) data and code assets in verifiably protected and isolated computing environments. No computing entity has access to these isolated and protected environments. Code and data assets outside the secure enclaves are encrypted (and thus protected) using keys generated by programs inside the secure enclave. Once the encrypted assets enter the secure enclave, they may be decrypted using (private) keys that are known and remain accessible only inside the secure enclave. Executions occurring inside the enclave generated verifiable audit logs that are immutable. These logs attest to the integrity of the secure enclave and the executions occurring inside the enclave.
Thus, secure enclave-based systems, such as the SafeLiShare Dynamic Data Security platform, provide capabilities that, when used, assure that policies attached to shared data and code assets are faithfully carried out by receiving organizations and programs.
5. The Output Management Phase
In the output management phase, care must be exercised to provide the results of data processing to authorized programs and entities only. One way to achieve this goal is to assign a role to the output receiver and specify access policies to the output receiver’s role.
SafeLiShare’s platform requires an output role and policy to be specified before an execution can be initiated. Any output resulting from execution is encrypted to the policy of the output receiver’s role by a computing process running in a secure enclave. Thus, the output exiting a secure enclave is encrypted and can only be decrypted by the output receiver entity.
Potential Digital Privacy Violation
The CLOUD Act is a U.S. federal law designed to promote international cooperation in law enforcement and cybercrime investigations by allowing authorities to access data stored in the cloud, regardless of where it originates from and who owns it. This article will explore how the CLOUD Act affects digital privacy and security for individuals in the U.S., as well as detail other key points from the legislation that viewers should be aware of. Even though the data processing agreements are typically formed with AWS, Azure, GCP, and SaaS providers, the CLOUD Act allows the US government to access data on U.S. companies’ cloud storage, regardless of where the cloud region is located.
To be compliant with the CLOUD Act and allow regulatory access to stored encrypted assets, data owners may securely share the decryption keys with regulatory bodies. One way of achieving such control, as provided by SafeliShare’s Dynamic Data Security (DDS) platform, is as follows.
A regulatory body and a data owner use SafeLiShare’s DDS to create a pair of interconnected and interrelated secure enclaves that are used to share data objects such as decryption keys.
The data owner encrypts a data encryption key(DEK) of an encrypted data asset using a public key encryption key(KEK) provided by its secure enclave. That is, the public KEK is generated from within a secure enclave whose corresponding private KEK remains inside the enclave. The encrypted DEK is then shared with the regulatory body whose secure enclave receives the private KEK (through a secure encrypted channel, e.g., using MTLS) from the data owner’s secure enclave. The receiving enclave decrypts the encrypted DEK, and uses the DEK to decrypt the encrypted data asset.
For information on how DEK and KEK interact, check the reference [https://security.stackexchange.com/questions/93886/dek-kek-and-master-key-simple-explanation](https://security.stackexchange.com/questions/93886/dek-kek-and-master-key-simple-explanation)
In this manner, both parties, the regulatory body, and the data owner are (cryptographically) assured that the shared data asset remains secure and always under the data owner’s policy control.
For customers in certain industries, such as the public sector, healthcare, and financial services, concerns about security can lead to a preference for on-premises deployment or virtual private clouds. These solutions require additional set-up time and have higher initial costs compared to cloud-based deployments. Additionally, maintenance and updates of these systems incur additional costs that the SaaS provider and the customer have to bear throughout the customer’s lifetime. For real-world use cases and design guidelines, follow up on Linkedin or email info@safelishare.com for our SaaS Data Security Use Cases with Confidential Computing.
To conclude, TEEs provide organizations using SaaS with high levels of security while reducing their overall IT burden. By deploying confidential computing to safeguard customer information and transactions hosted within a cloud platform, organizations gain complete control over who accesses what parts of the application―ensuring those interactions remain private between only authorized parties.
SafeLiShare provides runtime secure enclave provisioning that is designed for modern SaaS providers to securely encrypt and protect their customer assets — applications, code, and data. SasS providers can utilize SafeLiShare’s Safelet and SafeStream to turn public cloud workflows into private cloud workflows with encryption in use and offer a premium tier of service with high confidentiality in major cloud environments with TEE support.
We will be sharing a few integration use cases in our next blog, so stay tuned.
For SaaS providers interested in seeing how the integration works and a demo of SafeLiShare’s confidential computing solution, contact us at https://safelishare.com/contact or email info@safelishare.com.
Suggested for you
February 21, 2024
RSAC 2024: What’s New
SafeLiShare unveils groundbreaking AI-powered solutions: the AI Sandbox and Privacy Guard in RSAC 2024

February 21, 2024
Cloud Data Breach Lifecycle Explained
During the data life cycle, sensitive information may be exposed to vulnerabilities in transfer, storage, and processing activities.

February 21, 2024
Bring Compute to Data
Predicting cloud data egress costs can be a daunting task, often leading to unexpected expenses post-collaboration and inference.

February 21, 2024
Zero Trust and LLM: Better Together
Cloud analytics inference and Zero Trust security principles are synergistic components that significantly enhance data-driven decision-making and cybersecurity resilience.