Secure Application Runtime Environments with Secure Enclaves
Data Breaches in Application Runtime Environments Explained
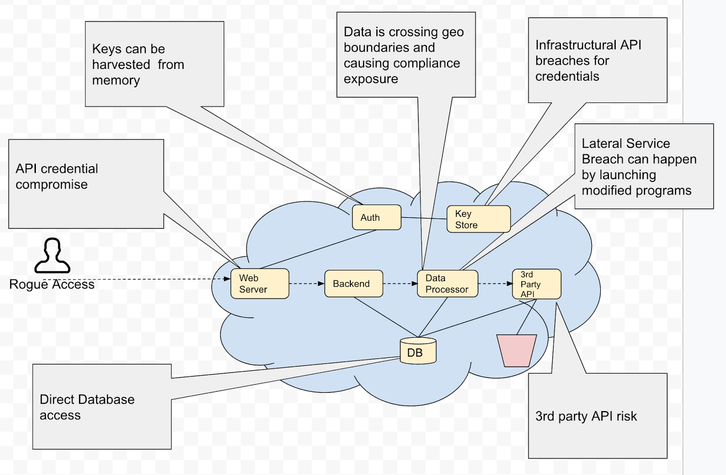
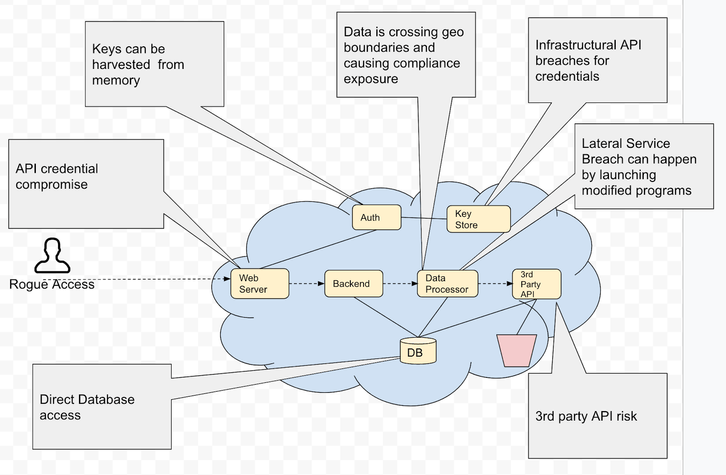
Corporations are being threatened by a new type of cyber attack that originates from within the business itself. This internal threat comes in the form of runtime, which is something companies routinely utilize but may not consider as a potential risk. Malware, spyware and ransomware have long been external security threats, but runtime brings a whole new set of dangers to be aware of.
All software programs use runtime, whether on a company network, cloud-based services, or mobile apps. Threat actors have learned to take advantage of runtime by planting harmless pieces of data into application servers. These can include emails, productivity tools, mobile apps, social media and IoT devices. During runtime when the program is launched by a user, this data turns into malicious code. Applications send out this information to different locations once they are executed.
Malicious code triggers an application to misdirect data to the RAM and CPU’s memory. This allows threat actors to gain access and steal any type of data. Threat actors attempt to escalate privileges and add further malicious code in order to view all available information. It is believed that elite code developers are responsible for this complicated runtime manipulation process.
Runtime attacks are still early in their development, but technology is quickly evolving. Bolster your business’s security before it becomes a target of more powerful runtime threats. A cyber-attack can occur when organizations neglect the basics such as software updates and patches. Avoid the risk by improving security immediately with our services.
Cloud Data Breaches and Vulnerabilities
Cloud data breaches and vulnerabilities occur when there is an unauthorized access to sensitive information stored in the cloud. This can happen due to a variety of reasons, including misconfiguration of cloud resources, insecure authentication and authorization methods, or unpatched security issues. Malicious actors can exploit these weaknesses to steal this data, leading to privacy and financial losses. Securing cloud resources is an essential step for protecting against such incidents.
SDLC runtime vulnerabilities occur when the application moves from development to production and becomes vulnerable to an attack. These vulnerabilities are essentially flaws in the design and coding of applications that hackers can exploit either during or after deployment. Examples of such vulnerabilities include unpatched software, weak authorisation process, lack of input validation, poor encryption algorithms and other insecure programming practices.
Confidential Computing to Secure Computation and Data from Inside Out
Security controls involve each of the stages that are part of the software development life cycle (SDLC): requirements, design, coding/testing, deployment, and monitoring. Examples of security controls include using code reviews to detect coding vulnerabilities and implementing automated testing procedures to identify and mitigate any potential risks before they result in an attack. Security controls can also be implemented during deployment through network defenses like firewalls as well as access control mechanisms such as authentication measures. Continuous monitoring and auditing ensures that any security threats or issues are identified and remedied immediately.
Suggested for you
February 21, 2024
RSAC 2024: What’s New
SafeLiShare unveils groundbreaking AI-powered solutions: the AI Sandbox and Privacy Guard in RSAC 2024

February 21, 2024
Cloud Data Breach Lifecycle Explained
During the data life cycle, sensitive information may be exposed to vulnerabilities in transfer, storage, and processing activities.

February 21, 2024
Bring Compute to Data
Predicting cloud data egress costs can be a daunting task, often leading to unexpected expenses post-collaboration and inference.

February 21, 2024
Zero Trust and LLM: Better Together
Cloud analytics inference and Zero Trust security principles are synergistic components that significantly enhance data-driven decision-making and cybersecurity resilience.