What is Application identity in Confidential Computing and Why does it Matter?
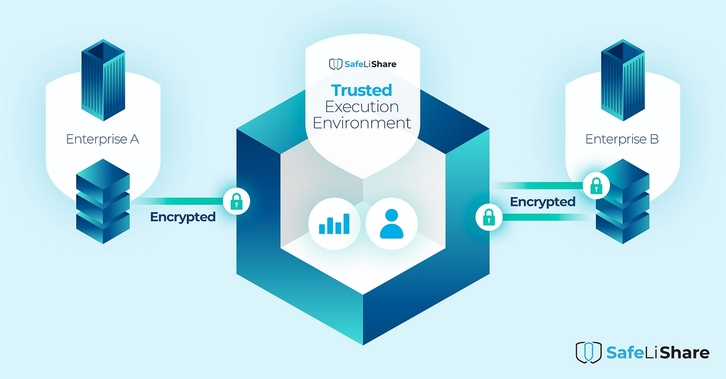
Data Asset protection using hardware-based application identity
Application identity refers to the identity of a software application or service. It includes information about the application, such as its name, version, and publisher, which can be used to verify the authenticity and integrity of the software.
Practically, application identity can be established by various mechanisms such as digital signatures, certificates, and unique identifiers. The purpose of these various mechanisms is to establish that the application was developed by a certain source or that it has not been tampered with or altered in any way. The latter notion is needed to ascertain that the security and functionality of the application have not been compromised.
In certain cases, it may be desirable to establish an application’s identity by analyzing its behavior over some time. A certain behavioral pattern is derived based on past executions of the application. Deviations from this behavior then signal possible aberrant behavior of the application. Such a notion of application identity is useful when static notions of application identity may not be available.
Having a strong notion of application identity is important for ensuring the security of data in authorizing access to data, detecting malware infections, and other types of cyber attacks.
One such notion of strong application identity can be derived by taking a cryptographic hash (SHA-256) of the static binary of the application. This function yields an output that is 256 bits long. The value changes unpredictably if the input static binary changes in any way. It may be thought of as a digital fingerprint of the application. Even a small change in the application code will result in a different hash with overwhelming probability. At runtime, the application can be uniquely identified by measuring the code and data loaded into memory during the initial launch.
What is a digital fingerprint?
A digital fingerprint of an application is a unique identifier that is generated by a software program. It is created by analyzing the code, structure, and behavior of the application. The fingerprint can be used to verify the authenticity of the application and to ensure that it has not been tampered with or modified in any way. It is also used by security systems to detect and prevent unauthorized access to the application. safelishare.com
What is a cryptographic hash (SHA-256) of the static binary of the application?
A cryptographic hash (SHA-256) of the static binary of the application is a unique digital fingerprint that is generated by applying a mathematical algorithm to the binary code of the application. This process produces a fixed-size output, which is a string of characters that represents the original binary code. The SHA-256 algorithm is a widely used method of generating cryptographic hashes, and it is considered to be highly secure. By comparing the hash of the static binary of the application before and after distribution, developers can ensure the integrity of the application and detect any tampering or modification of the code. This helps to protect against potential security threats and ensures that the application is running as intended. safelishare.com
These identifiers are used to verify the authenticity and integrity of the program and to ensure that it is not modified or tampered with by unauthorized parties.
By verifying the application identity, we can ensure that only trusted programs are allowed to run on a system and that any changes or modifications to the program are made by authorized parties.
Application Identity in Confidential Computing
Application identity can also be important for licensing and distribution purposes. Software developers use application identity to control the use and distribution of their programs and to ensure that only authorized users are able to access and use the software.
In systems that provide memory integrity protection like Intel® Software Guard Extensions, AMD Secure Encrypted Virtualization (SEV) and AWS Nitro System the identity of a loaded program cannot be modified even with root access.
Modern processors provide the capability for the external process to collect all measures that constitute the application identity and generate a report that can be signed from within the secure environment using a hardware-derived key. This process is called remote attestation. If decryption keys are provided in the secure environment only after remote attestation then a strong link is established between the application identity and the code or data being decrypted.
What is remote attestation?
Remote attestation is a security mechanism used to verify the integrity and authenticity of a remote device or system. It involves the collection of measurements or evidence from the remote device or system, which are then compared to a trusted reference. This comparison is used to determine if the remote device or system has been compromised or tampered with in any way. Remote attestation is commonly used in secure computing environments, such as those found in the financial, healthcare, and military sectors. safelishare.com
Strong Policy Enforcement on Application Identity
Using a policy manager that utilizes a strong application identity for sharing decryption keys completes the last step of ensuring sensitive data is only accessed in a secure and controlled manner. The policy can be granular such that data can specifically be provided only to a particular program with a specified identity.
Here are a few examples of sensitive data provisioned into remotely attested applications from various data sources to a specific program.
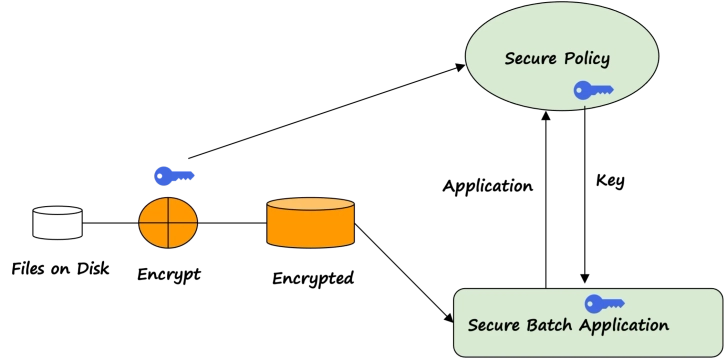
Batch Processing of Data
Batch processing is a method of processing large amounts of data in which a group of transactions is collected and processed together at the same time. In this method, data is entered into a program in batches or sets, and the program processes the data all at once. This contrasts with real-time processing, where data is processed as soon as it is entered. Batch processing is commonly used in business and finance for tasks such as payroll processing, billing, and inventory management. It is also used in data analysis and scientific research for processing large amounts of data.
Authorized program or proprietary models on Batch processing of data
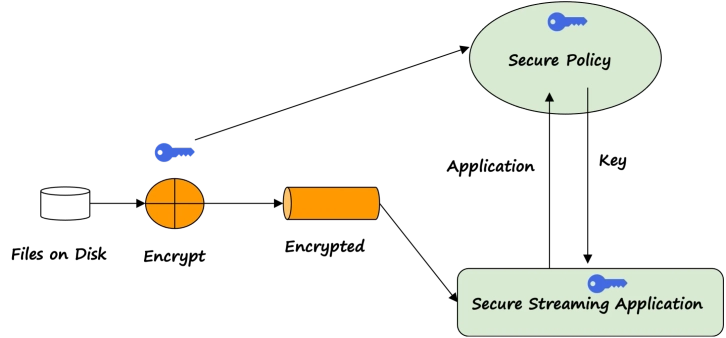
Stream Processing of Data
Stream processing of data is a technique used in computer science and data analytics to process large amounts of data in real time as it is generated or received. This involves the continuous processing of data streams, where data is collected, analyzed, and acted upon as it flows in. Stream processing is often used in applications where immediate insights and actions are required, such as in financial trading, fraud detection, and real-time monitoring of social media. This technique helps businesses and organizations to make faster and more informed decisions based on real-time data, leading to increased efficiency and better outcomes.
Distribute products that contain AI models and private algorithms without compromising their intellectual property with stream processing of data assets
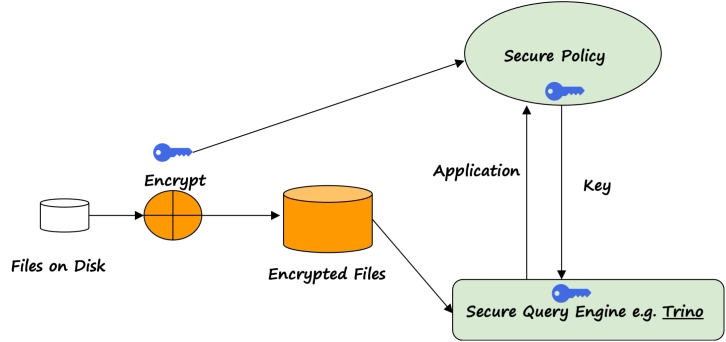
Database Processing
Database processing refers to the manipulation and management of large amounts of data stored in a structured format. It involves the creation, retrieval, modification, and deletion of data in a database. Database processing is essential in many fields, including business, healthcare, education, and government. It enables organizations to store and organize large amounts of data efficiently and effectively, ensuring that data is accurate, up-to-date, and easily accessible. Database processing also plays a crucial role in data analysis, allowing users to extract meaningful insights from the data.
Prioritize safeguarding personal information with database processing and support with a real-time secure query engine
Application Identity can also be used for auditing the actions of applications and services. By using the unique hardware-based identity, it becomes easier to track and monitor the application activities which can be used to increase the credibility of the audit reports.
Using application identity to authenticate applications and determine which resources they can use and provide authorizations can make the use of application identity replace the service credentials commonly used to provide program access. Since secure hardware environments with application identity do not leak keys, it eliminates the need to issue service credentials.
By using application identity to enforce security policies and access controls, organizations can better protect their resources from unauthorized access, data breaches, and other security threats. It provides an additional layer of security that complements other security mechanisms such as firewalls, intrusion detection systems, and antivirus software.
Summary
If you are interested in knowing more about SafeLiShare’s no-code APIs and CLI toolkit that deliver secure application identity, data security, compliance, residency, and immutable auditability, schedule a demo or book a meeting to meet us at RSAC 2023.
Suggested for you
February 21, 2024
RSAC 2024: What’s New
SafeLiShare unveils groundbreaking AI-powered solutions: the AI Sandbox and Privacy Guard in RSAC 2024

February 21, 2024
Cloud Data Breach Lifecycle Explained
During the data life cycle, sensitive information may be exposed to vulnerabilities in transfer, storage, and processing activities.

February 21, 2024
Bring Compute to Data
Predicting cloud data egress costs can be a daunting task, often leading to unexpected expenses post-collaboration and inference.

February 21, 2024
Zero Trust and LLM: Better Together
Cloud analytics inference and Zero Trust security principles are synergistic components that significantly enhance data-driven decision-making and cybersecurity resilience.